Notepad is the simplest text editor provided by Microsoft in every version of Windows. It is helpful when we want to create a quick note. The files created by Notepad are saved in .txt format which is supported by every text editor. So, the files created by Notepad are compatible to open, edit and modify everywhere.
People generally consider Notepad simpler than what it is. But readers, Notepad is light-weight text-editor but saying it “simpler” would be wrong because it can open many unknown extensions files and Notepad itself hold many amazing commands, tricks and hacks to make it more productive for you.
Today, I am going to share 10 amazing Notepad Tricks & Hacks that you can use to get most out of Notepad and amaze your friends.
1. Create Diary on Notepad
This Notepad trick will allow you to create Notepad note in such a format that whenever you edit your note, it will get saved with date and timestamp automatically. To do this, follow these steps:
- Open Notepad
- Type .LOG in first line.
- Save the file as Log.txt
- Now, write something to the file and it will automatically get saved with edited date and time.
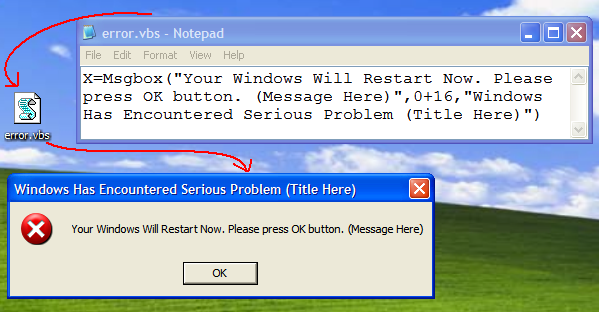
2. Create Fake Windows Errors With Notepad
This is another very cool Notepad trick that allows you to create Fake error messages. You can create Fake error message with any message. To do this, follow these steps:
- Open Notepad
- Type X=Msgbox(“Message Here”,0+16,”Title Here”)
- Replace Message Here and Title Here with your Error Message and Error-Window Title respectively.
- Save the file with error.vbs.
- Now, click the file and you’ll get your custom-made Windows error message.
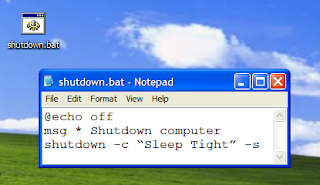
3. Force Shutdown Your Windows
This trick will let you force shutdown your Windows in a single-click. So, if you don’t want to waste three clicks (Start >> Turn Off Computer >> Turn Off), this trick will help you in that. To do this:
- Open Notepad
- Paste @echo off in first line.
- Paste msg * Shutdown computer in second line.
- Paste shutdown -c “Sleep Tight” -s in third line
- Save the file with .BAT extension. For example, shutdown.bat
- Click on your file and it will automatically shutdown your Windows.
You can imagine the disaster that may happen if you’ll put this file at Windows Startup
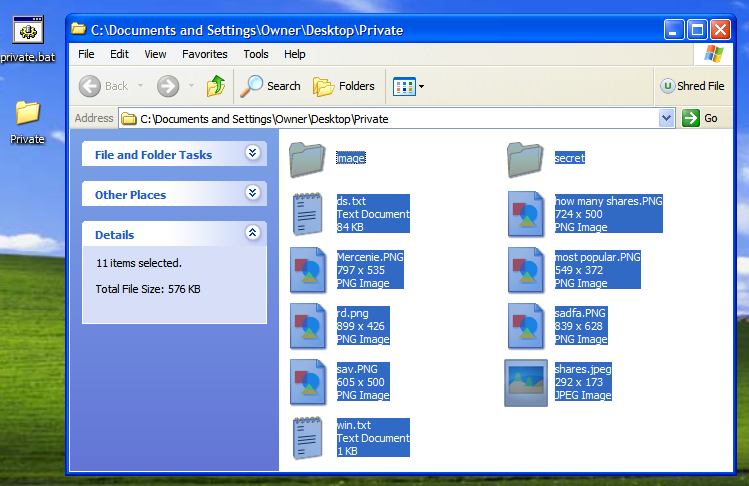
4. Create Password-protected Folder using Notepad
Why to use any folder-locking software when your simple text editor, Notepad can lock your folders? To use this Notepad tricks, follow these steps:
- Open Notepad
- Copy the following code:
@ECHO OFF
title Folder Private
if EXIST “Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}” goto UNLOCK
if NOT EXIST Private goto MDLOCKER
:CONFIRM
echo Are you sure you want to lock the folder(Y/N)
set/p “cho=>”
if %cho%==Y goto LOCK
if %cho%==y goto LOCK
if %cho%==n goto END
if %cho%==N goto END
echo Invalid choice.
goto CONFIRM
:LOCK
ren Private “Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}”
attrib +h +s “Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}”
echo Folder locked
goto End
:UNLOCK
echo Enter password to unlock folder
set/p “pass=>”
if NOT %pass%== techparadise goto FAIL
attrib -h -s “Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}”
ren “Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}” Private
echo Folder Unlocked successfully
goto End
:FAIL
echo Invalid password
goto end
:MDLOCKER
md Private
echo Private created successfully
goto End
:End
title Folder Private
if EXIST “Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}” goto UNLOCK
if NOT EXIST Private goto MDLOCKER
:CONFIRM
echo Are you sure you want to lock the folder(Y/N)
set/p “cho=>”
if %cho%==Y goto LOCK
if %cho%==y goto LOCK
if %cho%==n goto END
if %cho%==N goto END
echo Invalid choice.
goto CONFIRM
:LOCK
ren Private “Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}”
attrib +h +s “Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}”
echo Folder locked
goto End
:UNLOCK
echo Enter password to unlock folder
set/p “pass=>”
if NOT %pass%== techparadise goto FAIL
attrib -h -s “Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}”
ren “Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}” Private
echo Folder Unlocked successfully
goto End
:FAIL
echo Invalid password
goto end
:MDLOCKER
md Private
echo Private created successfully
goto End
:End
- techparadise written in red is password. Change it to your own password.
- Save the file as private.bat with File Type As All Files (*.*).
- Now, when you click private.bat, it will create a Private folder. Move your private files, documents and folders here.
- Close Private folder.
- Now, no one will be able to open the folder without the password.
5. Make Computer To Speak Your Sentence
This Notepad trick will make computer to speak whatever you type in the provided text-box. To use this trick, follow these steps:
- Open Notepad
- Copy & paste this command:
Dim message, sapi
message=InputBox(“What do you want me to say?”,”Speak to Me”)
Set sapi=CreateObject(“sapi.spvoice”)
sapi.Speak message
message=InputBox(“What do you want me to say?”,”Speak to Me”)
Set sapi=CreateObject(“sapi.spvoice”)
sapi.Speak message
- Save the file as speak.vbs.
- Double-click the file and it will open a prompt. Enter the sentence you want your computer to speak
- Click OK and Notepad will speak the sentence for you.
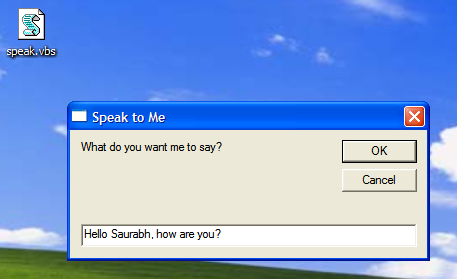
Note – In case, if you encounter error, re-type all the quotes and this notepad trick will work fine.
6. Make CD Drive Open & Close Again and again
This notepad prank will make your CD drive open and close again and again continually. To use this notepad trick, use these following steps:
- Open Notepad
- Enter following command:
Set oWMP = CreateObject(“WMPlayer.OCX.7”)
Set colCDROMs = oWMP.cdromCollection
do
if colCDROMs.Count >= 1 then
For i = 0 to colCDROMs.Count – 1
colCDROMs.Item(i).Eject
Next
For i = 0 to colCDROMs.Count – 1
colCDROMs.Item(i).Eject
Next
End If
wscript.sleep 5000
loop
Set colCDROMs = oWMP.cdromCollection
do
if colCDROMs.Count >= 1 then
For i = 0 to colCDROMs.Count – 1
colCDROMs.Item(i).Eject
Next
For i = 0 to colCDROMs.Count – 1
colCDROMs.Item(i).Eject
Next
End If
wscript.sleep 5000
loop
- Save your notepad file as cdopen.vbs
- Now, open cdopen.vbs and it will start the process to continuously open and close CD drive.
To stop the process, open Task Manager by pressing Alt+Ctrl+Del and stop cdopen.vbs process.
7. Create Matrix Raining Code Screen
Have you watched the movie, “Matrix”? You might have seen string of green characters appearing at the screen randomly. We are going to do something similar with the help of Notepad. To use this Notepad trick, follow these steps:
- Open Notepad.
- Type this command:
@echo off
color 02
:start
echo %random% %random% %random% %random% %random% %random% %random% %random% %random% %random%
goto start
color 02
:start
echo %random% %random% %random% %random% %random% %random% %random% %random% %random% %random%
goto start
- Save the file as Matrix.bat
- Click on Matrix.bat and the show begins.
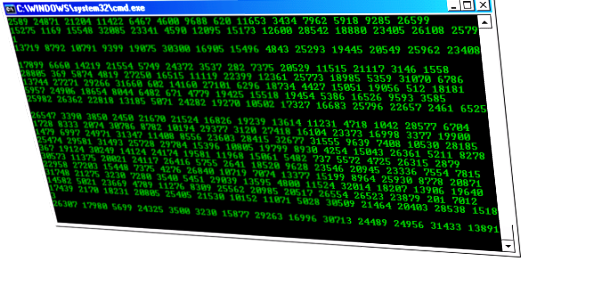
Alternatively, you can use this code for different effect:
@echo off
:a
color 2
echo 1 1 1 0 1 0 0 0 1 1 1 1 0 0 0 1 1 0 0 1 0 0 0 1 1 0 1 0 1 0 0 0 1 1 1 1
ping localhost -n 1 > nul
echo 1 1 0 1 1 1 0 0 0 1 0 1 a f h 0 0 0 1 0 1 1 0 0 1 1 1 0 0 1 0 1 0 0 1 1 0
echo 1 0 0 1 1 0 9 8 1 2 0 1 9 9 2 1 1 1 0 0 1 0 1 1 1 0 1 1 0 1 0 0 0 1 0 1 1
ping localhost -n 1 > nul
echo 0 1 0 0 0 1 0 0 0 1 0 0 0 1 0 1 0 0 1 0 1 0 1 1 0 1 0 0 0 01 0 1 0 0 1 0
ping localhost -n 1 > nul
echo 1 0 1 1 1 0 1 1 0 9 1 1 2 1 1 0 9 1 0 5 7 7 8 7 8 1 3 2 1 2 1 2 3 2 1 3 4
ping localhost -n 1 > nul
echo 1 1 1 0 1 0 0 1 0 0 0 1 1 1 0 0 1 1 1 4 1 2 1 1 2 0 1 0 1 2 2 1 0 1 1 0 1
goto a
:a
color 2
echo 1 1 1 0 1 0 0 0 1 1 1 1 0 0 0 1 1 0 0 1 0 0 0 1 1 0 1 0 1 0 0 0 1 1 1 1
ping localhost -n 1 > nul
echo 1 1 0 1 1 1 0 0 0 1 0 1 a f h 0 0 0 1 0 1 1 0 0 1 1 1 0 0 1 0 1 0 0 1 1 0
echo 1 0 0 1 1 0 9 8 1 2 0 1 9 9 2 1 1 1 0 0 1 0 1 1 1 0 1 1 0 1 0 0 0 1 0 1 1
ping localhost -n 1 > nul
echo 0 1 0 0 0 1 0 0 0 1 0 0 0 1 0 1 0 0 1 0 1 0 1 1 0 1 0 0 0 01 0 1 0 0 1 0
ping localhost -n 1 > nul
echo 1 0 1 1 1 0 1 1 0 9 1 1 2 1 1 0 9 1 0 5 7 7 8 7 8 1 3 2 1 2 1 2 3 2 1 3 4
ping localhost -n 1 > nul
echo 1 1 1 0 1 0 0 1 0 0 0 1 1 1 0 0 1 1 1 4 1 2 1 1 2 0 1 0 1 2 2 1 0 1 1 0 1
goto a
8. Make Your Keyboard LED Dance
Your keyboard has three LEDs above numpad of Scroll Lock, Caps Lock and Num Lock. This Notepad trick will make those three LED continually on and off, creating dancing effects. To do this, follow these steps:
- Open Notepad
- Enter following code
Set wshShell =wscript.CreateObject(“WScript.Shell”)
do
wscript.sleep 100
wshshell.sendkeys “{CAPSLOCK}”
wshshell.sendkeys “{NUMLOCK}”
wshshell.sendkeys “{SCROLLLOCK}”
loop
do
wscript.sleep 100
wshshell.sendkeys “{CAPSLOCK}”
wshshell.sendkeys “{NUMLOCK}”
wshshell.sendkeys “{SCROLLLOCK}”
loop
- Save the file as Dance.vbs
- Click the file and your all three LED lights will start dancing.
To stop, Shut down or Log off your PC.

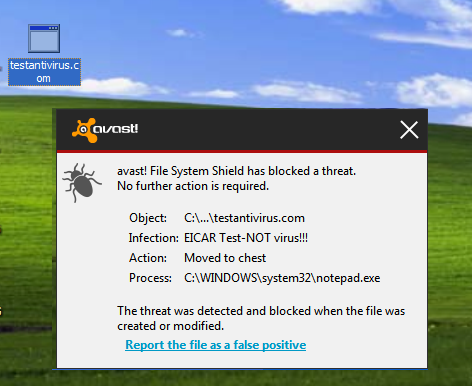
9. EICAR Test File: Test Your Antivirus
Do you want to check if your Antivirus’ real-time protection is working correctly or not? Then this European Institute for Computer Antivirus Research (EICAR) code will help you in that.
- Open Notepad
- Copy this code: X5O!P%@AP[4PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*
- Save the with .COM extension. For example, testantivirus.com
If your antivirus’ real-time protection is working perfectly, it will show you alert and quarantine the file by considering it malware.
10. Bush Hid The Facts
This is very simple but the most popular Notepad trick. To use this notepad trick, follow these steps:
- Open Notepad
- Type BUSH HID THE FACTS
- Save that file
- Open it again & see. Amazing?
Alternatively, you can use this app can break.
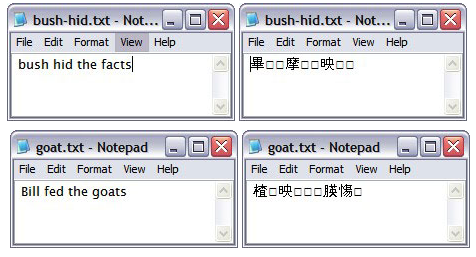
What happens?
You might have seen that reopening the file will get show you some unicode characters instead of what you typed (Bush hid the facts or this app can break).
Why this happens?
Both the patterns have characters string of length 4-3-3-5 which seems to cause bug in Windows PC. So, this trick works